Now we know. John Podest’s email was purloined by a network of Russian hackers capitalizing on a near universal weakness of all computer systems: a careless human.
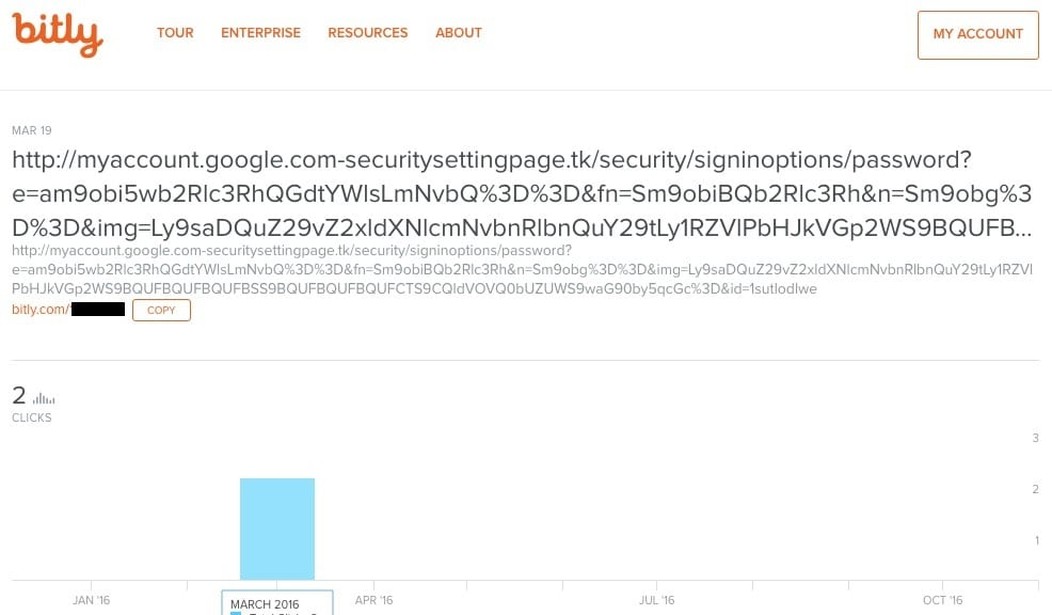
On March 19 of this year, Hillary Clinton’s campaign chairman John Podesta received an alarming email that appeared to come from Google.
The email, however, didn’t come from the internet giant. It was actually an attempt to hack into his personal account. In fact, the message came from a group of hackers that security researchers, as well as the US government, believe are spies working for the Russian government. At the time, however, Podesta didn’t know any of this, and he clicked on the malicious link contained in the email, giving hackers access to his account.
Months later, on October 9, WikiLeaks began publishing thousands of Podesta’s hacked emails. Almost everyone immediately pointed the finger at Russia, who is suspected of being behind a long and sophisticated hacking campaign that has the apparent goal of influencing the upcoming US elections. But there was no public evidence proving the same group that targeted the Democratic National Committee was behind the hack on Podesta—until now.
The data linking a group of Russian hackers—known as Fancy Bear, APT28, or Sofacy—to the hack on Podesta is also yet another piece in a growing heap of evidence pointing toward the Kremlin. And it also shows a clear thread between apparently separate and independent leaks that have appeared on a website called DC Leaks, such as that of Colin Powell’s emails; and the Podesta leak, which was publicized on WikiLeaks.
All these hacks were done using the same tool: malicious short URLs hidden in fake Gmail messages. And those URLs, according to a security firm that’s tracked them for a year, were created with Bitly account linked to a domain under the control of Fancy Bear.
It is actually a bit more embarrassing than “clicked on the malicious link.” The link spoofed a Google sign-in page and Podesta gave the hackers his userid and password. Read the whole story, I’d like to quote more of it but it isn’t fair to deprive the author of the clicks.
CTU researchers observed the first short links targeting hillaryclinton.com email addresses being created in mid-March 2016; the last link was created in mid-May. During this period, TG-4127 created 213 short links targeting 108 email addresses on the hillaryclinton.com domain. Through open-source research, CTU researchers identified the owners of 66 of the targeted email addresses. There was no open-source footprint for the remaining 42 addresses, suggesting that TG-4127 acquired them from another source, possibly other intelligence activity. [italics are mine.]
The identified email owners held a wide range of responsibilities within the Hillary for America campaign, extending from senior figures to junior employees and the group mailboxes for various regional offices. Targeted senior figures managed communications and media affairs, policy, speech writing, finance, and travel, while junior figures arranged schedules and travel for Hillary Clinton’s campaign trail.
So there is a lot of email out there waiting to be released because you can bet that Podesta was not the only person who fell for the scam.
If there was any doubt that the FSB or GRU were up in this to their eyebrows, that doubt has been dispelled.










Join the conversation as a VIP Member